If you believe the futurologists, then the Internet of Things (IoT) is going to be the next big thing. Depending on who you listen to, by 2020 there will be up to 50 billion connected devices, an order of magnitude greater than the number of mobile phones.
By Nick Hunn
If you believe
the futurologists, then the Internet of Things (IoT) is going to be the next
big thing. Depending on who you listen to, by 2020 there will be up to 50
billion connected devices, an order of magnitude greater than the number of
mobile phones. You can already see the start of that, whether it’s smart
meters, connected information signs, or the increasing number of fitness devices, like Samsung Gear,
Apple Watch, Moto 360, Google Glass, Fitbit and Nike’s Fuel wristband. To get a
better idea of what else may be emerging to make up that number, a good place
to start is Kickstarter – the website for crowd-sourced funding for such
projects. It shows that a significant
number of potential start-ups are looking for money to produce a bewildering
array of gateways and sensors.
The Concept of
Physical Security Controls:
A range of physical
controls can be implemented to help increase security. These controls are put
in place to ensure that only authorized individuals can access certain areas or
perform specific actions. Network cabling security should be considered when
initially setting up wiring closets and whenever upgrades are performed.
Cabling should be routed through the facility so that it cannot be tampered
with. Unused network drops should be disabled and all cable access points
should be secured, so that individuals cannot install sniffers or eavesdrop on
network communications.
Another
important concern is controlling individuals as they move throughout a
facility. Most organizations use card keys, badges, smart cards, or other IDs
to control the flow of traffic. This category can be divided into two broad
groups. The first category is ID cards, which do not contain electronics and
are very low tech. ID cards typically contain a photograph of an individual to
verify their identity, and are used in many organizations.
The second
category is intelligent access control devices that make access decisions
electronically. There are two subcategories of these devices: contact and contactless.
Contact access
cards require users to slide their card through a reader. These cards come in
several different con-figurations, including:
- Active Electronic - Can transmit electronic data
- Electronic Circuit - Has an electronic circuit embedded
- Magnetic Stripe -Contains rows of copper strips
- Optical-coded - Contains laser-burned pattern of encoded dots.
Contact-less
cards function by proximity (e.g., radio frequency ID [RFID]). An RFID is a small
electronic device comprised of a microchip and an antenna. An RFID tag can be designed
as an active device (i.e., a battery or power source is used to power the
microchip) or as a passive device - Passive devices have no battery; they are
powered by a RFID reader. The reader generates an electromagnetic wave that
induces a current in the RFID tag. There are also semi-passive devices that use
batteries to power the microchip, but transmit using the energy from the card
reader. When users are allowed into specific areas of a facility, it does not
mean that they should have access to all of the systems located there. That’s
why strong system access controls are so important. Complex passwords or
biometric systems can help, as well as multi-factor authentication (e.g., ATM
bank cards). Banks require you to have an ATM card and a pin number in order to
access funds or account information.
Even with these
physical controls in place, misuse and intrusions can still occur; therefore,
it is important to use IDSes. Physical intrusion detection includes the
components and systems installed to detect misuse or unauthorized intrusion.
Physical IDSes are designed around one or more sensor types. Motion detectors
can be triggered from audio, infrared wave pattern, or capacitance. These
detectors use passive infrared and are usually mounted in the corners of rooms
or used as security lights. Motion detectors send out a series of infrared beams
that cover an area with protection.
Other types of
sensors used with IDSes include photoelectric sensors and pressure-sensitive devices.
Pressure sensitive devices are sensitive to weight. They measure changes in resistance
to trigger alerts, and are good for protecting small areas. Glass breakage
sensors are another component of IDSes. If someone breaks a window or attempts
to pry it open, the sensor triggers an alarm. IDSes are another piece of total
security control. The idea is to place them in key areas that contain critical
assets or in areas most likely to be violated by intruders. IDSes are not perfect
and produce their own share of false positives. Every time an alarm goes off, someone
must respond and verify the event. If IDS is tied to a police department or
fire department, false alarms can result in some hefty fines.
The Evolving
Concept of IoT with respect to Wireless Security Ecosystem
The rise of
these connected devices, which is the vanguard of the Internet of Things, is
really exciting. But it’s mostly
happening with low cost, proprietary wireless chips. The growth of products from new start-ups and
Kickstarter projects are being fuelled by silicon vendors who are bringing
highly integrated wireless processor chips to the market. The tools that support these chips and reference
designs make it very easy to get prototypes up and running and then take the
resulting products to market. They’re
wonderful devices to design with, but they generally leave any security
implementation to the designer. And
wireless security is difficult. So where
does an IoT designer start?
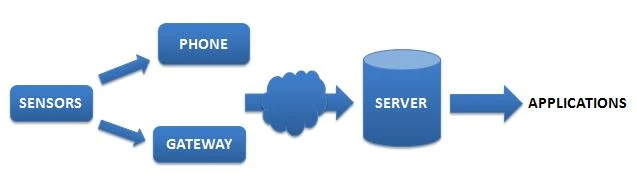
Image Attribute: IoT Workflow / Source: www.nickhunn.com
Most wireless
sensor systems can be broken down into three distinct parts – the sensor, which
generates the data; the gateway (which may be a mobile phone) that takes sensor
data and transmits it over the Wide Area Network (WAN) and the server/database which receives, stores
and processes it. The traffic (at a high
level) may be bidirectional, with control signals going back down to the
sensor. And the WAN access may be an
integral part of the sensor, as is the case where it contains a cellular
modem. But in most cases it’s not.
Where it is
separate, there are typically two wireless links – the short range, local or
personal area network and the wide area connection, which is generally either
cellular or broadband. The chances are
that any security implementation is different over both, and that there’s not
any end-to-end security. Most systems
tend to be put together in a piecemeal “Lego” fashion, so security is at best only
link wide. There are some vocal advocates
of IP to the device, claiming that it plays to the end-to-end security model,
but I’m still to be convinced that IP and low power wireless make sensible
bedfellows. Which means that most real Machine-2-Machine (M2M) and IoT implementations are likely
to combine a number of different security schemes, without an overall
end-to-end security model?
If security is
important to you then one of the first things you need to do is to construct an
end-to-end security model. Even if you
think that it’s not important for your application, it’s still worth doing
this, so that you can demonstrate why you didn't need to implement it. The principle here is that you need to think
through what you are trying to protect and what the consequences of an attack
may be. The severity of risk may not be where you think it is. Too often we have seen massive overkill in a
sensor or gateway which then places secure data from multiple sources in an unsecured
server.
It is to be noted, how important it is to do this at an early stage of the design process,
as it affects the choice of protocols and chips. When it’s done early on, it adds little cost
or time to a project. Adding it as an afterthought
can cripple the cost of a product or service, or at worst send it back to the
drawing board.
The Concept of
RMADS - Risk Management and Accreditation Document Set
As soon as you
have decided what you want your product to do, and sketched out the overall
architecture, sit down and produce what the industry calls an RMADS. The philosophy
behind it is to ask what are the consequences of data being lost, corrupted or
injected at each stage. Each of these
three possibilities is important to consider.
And their relative importance will be different for different
applications.
Common sense
here really means thinking about fit for purpose. For many sensors around the home it may not
matter if they can be overheard. It may
matter more if someone can inject spurious packets, as that can lead to false
alarms, the transmission of incorrect data that gets back to the server or the
annoyance of something being turned on or off.
All of which can reduce customer confidence in your product as it makes
it look unreliable. An associated point
to consider is working out how to add new wireless devices to the network and
stop rogue ones being attached. Pairing
and authentication is one of the most difficult aspects of wireless, as ease of
use and security comes head to head. You also need to think about how to swap
out defective devices without leaving vulnerabilities, which essentially means
working out how to distribute link keys securely around your system.
At the gateway
you need to consider how you ensure that the sensor data gets back to the
server securely. This generally means
TLS, unless you have end to end security.
That’s not the way most IoT devices work today, as the community is
promoting simplicity, open hardware, open APIs and simple POST messages. That doesn’t means you can’t design secure
open systems, but you need to understand what level of security you’re being
offered and make sure you’re happy with it.
Once again, it’s about understanding what you’re implementing and
whether it meets your needs. Remember
that in most cases, commercial IoT products are only viable when the customer
can trust the way their data is being handled.
That’s a very different scenario from people experimenting with Arduinos
and open sensor projects. Each have
their place, and can extend into each other’s, but the inherent security levels
of each should not be confused.
Often the
biggest issue is at the server, where a lack of thought can expose the
data. As we regularly see, even large
companies who should know better don’t handle their passwords and
authentication robustly. And the bigger
the target, the more interesting it gets to hackers. If you’re designing a commercial system and
you’re lucky, it could catch the zeitgeist and grow beyond your wildest dreams
to become a significant part of those 50 billion devices. Some of the products being designed today are
probably destined to do that. At which
point any lack of security in their initial design will come back to haunt them
and their investors, which is another reason for getting it right at the
beginning.
About The Author:
Nick Hunn, Technology
evangelist, serial entrepreneur and developer with a broad view of both the
detail of technologies, the user experience and wider interplay of different
market solutions. Leading edge technology analysis, development and evangelism.
Speaker and conference chair within the wireless, smart energy, eHealth,
wearables, IoT, telematics and Big Data areas and author of numerous white
papers. He blogs at www.nickhunn.com
This article is
an abridged from a paper written by the author in year 2012 under the title – “Wireless
Security for the Internet of Things”.
This work is licensed under a Creative
Commons License.