As the United States (U.S.) foreign focus shifts from a region where there has been a general freedom of access for intelligence gathering assets, leaders must consider that many regions containing near-future threats do not grant U.S.forces the permissive access that they have become accustomed to.
By Jeff Cuddlington
As the United
States (U.S.) foreign focus shifts from a region where there has been a
general freedom of access for intelligence gathering assets, leaders must
consider that many regions containing near-future threats do not grant U.S.forces
the permissive access that they have become accustomed to. Developed nations
like Russia, China, North Korea, and Iran are among the locations that the
military and State Department once again consider to be top threats. These
potential threats simply will not allow foreign powers like the U.S.to have
complete freedom of movement and will actively work against attempted U.S. intelligence
operations.
Image
Attribute: Joint Operational Access Concept (JOAC) in a Anti-Access, Area Denial
Theatre
/ Source: McNeal & Associates
Simply put,
the act of an adversary to work against the actions of another defines what
anti-access or area denial environments are. More formally, the U.S Department
of Defense (DoD) Joint Operational Access Concept (JOAC) defines these terms:
“Anti-access (A2) refers to those actions and capabilities, usually long-range,
designed to prevent an opposing force from entering an operational area. Area
denial (AD) refers to those actions and capabilities, usually of shorter range,
designed not to keep an opposing force out, but to limit its freedom of action
within the operational area” (United States Department of Defense 2012, i).
This continues to be an ongoing concern for leaders as the 2014 “National
Intelligence Strategy of the United States of America” lists among its major
objectives that the IC will have develop strategies to operate in denied areas
(Office of the Director of National Intelligence 2014).
According to the
“Air-Sea Battle” concept, the general U.S. solution to the A2/AD issue is to
develop a network of integrated forces capable of defeating the enemy across
all modern war fighting domains: air, sea, land, space, and cyberspace (United
States Department of Defense 2013). This concept recognizes that adversary forces
will likely attack without warning and forward friendly forces will be in the
A2/AD environment from the outset of hostilities and must provide an immediate
and effective response.
While this
reflects one view of future complications, A2/AD can be defined in other ways.
Howard defines these denied areas as, “regions whose nations are characterized
by weak state structures” (Howard 2007, 2). While Howard approaches A2/AD from
a Human Intelligence (HUMINT) standpoint, I feel his definition does not necessarily apply to much of
the Middle East in a general intelligence perspective, a region characterized
by many countries with weak state structure but for the most part presenting
little A2/AD against the United States.
Regardless,
any state operating effective A2/AD could severely hinder U.S. operations in
that area, or even deter the U.S. and coalition partners from responding to
aggression in the first place (Krepinevich, Watts and Work 2003). The Center
for Strategic and Budgetary Assessments (CSBA) goes further with this reasoning
suggesting that America may be the cause of its own A2/AD problems, 8 stemming
from United States’ worldwide power projection and military pre-eminence
(Krepinevich, Watts and Work 2003). This suggests that there may be issues
inherent in Unites States foreign policy or other national ideals. Conversely,
some may argue that the “big brother” image of America forces some nations to
make significant expenditures in deterrence or self-defense, instead of
possibly more offensive actions. I feel America’s current foreign policy action
is creating more problems than it is solving. An aggressive and intrusive
foreign policy creates more barriers and friction among other nations, seeds
more conflict, and translates to increased difficulty, risk, and casualties when
conflicts do erupt.
It is important to be aware that not all of
the current, emerging, and evolving threats are alike— while developed and
modern nation-states have returned to the forefront of attention, there will
continue to be the threat of transnational terrorism. Developed countries such
as Russia, China, Iran, and North Korea have considerable access to advanced
missile and satellite technology permitting even regional rogue states the
ability to pre-target U.S. forward bases abroad and monitor deployment activity
(Krepinevich, Watts and Work 2003). By contrast, transnational terrorist cells
like al-Qaeda, Taliban, and Abu Sayyaf often operate beyond political borders,
blend in with the local populations, and maintain a low visibility. As such,
this category of threats requires a very different approach than with nation states.
China is one
of the most significant A2/AD threats at this time. China not only deters the
United States from deploying into the Western Pacific, but also threatens to
disrupt nearby operations such as around Taiwan or the South China Sea
(McCarthy 2010). While U.S. advanced fighters and bombers have inherent
advantages against China’s defenses, these aircraft are not immune and are very
limited in availability. A majority of American fighters, bombers,
reconnaissance aircraft, and cruise missiles remain extremely vulnerable.
China’s integrated air defense system is virtually impossible to penetrate with
current U.S. fourth-generation aircraft (McCarthy 2010). Furthermore, China is
expected to increase 9 its threat range with the development of the S-400
missile system, extending their air defense coverage out to over 200 nautical
miles (McCarthy 2010).
In 2007, China also demonstrated its ability to target
and shoot down orbital satellites when it shot down one of its own. This
capability could be easily carried out against U.S. satellites in a conflict,
severely degrading the U.S. view into the Chinese interior. The side that can
better collect, transmit, and exploit information while denying their enemy the
same will be the victor in war, a term called “information dominance,”
something that China has demonstrated they are well aware of (Cheng 2013).
While their strategic and operational concepts are of concern, China’s tactical
dimension focuses on destroying or damaging American capabilities with an array
of missiles and submarines (Cheng 2013). Staying out of China’s missile
envelope brings questions to the effectiveness of the upcoming F-35 with its
relatively short range. Clearly, the Chinese position is one of exclusion and
intent on keeping America or other adversaries away with formidable A2/AD.
Iran has a dangerous
influence over one of the most important commercial choke-points in the world:
the Straits of Hormuz. Iran also has a significant modern military capability
and robust A2/AD network. Should all-out conflict occur with Iran, the United
States has no close-in bases to operate fighters from, an important first step
in modern warfare (Gunzinger and Dougherty 2011). It would be assumed that in a
conflict with Iran, access to the Persian Gulf would be denied and Iran would
pressure its neighbours to deny U.S. access. Launching from an airbase in
Turkey or a carrier in the Arabian Sea, our closest guaranteed large-scale
basing opportunities, provides only partial coverage into Iran. Iran also has a
significant defensive advantage which will require detailed intelligence to
counter. While their command infrastructure prevents it from combining its air
defense systems into a truly integrated network, Iran’s A2/AD capabilities and
strategies are considered to be similar to China’s and produce a significant
threat to all U.S. ISR attempts (Gunzinger and Dougherty 2011).
Non-state
actors, such as transnational terrorist organizations, can also pose a threat.
Ballistic missile systems and advanced stealth fighters are not the only ways
to deter enemies. The cyberspace 10 domain has become a major front in modern
warfare and requires very little technology to be devastating. Cyber-information
warfare, distributed denial of service attacks, malicious software, and
financial/resource manipulation are only some of the effects that can severely
impair a fighting force. Electro-magnetic pulse weapons can be cheaply made and
be just as devastating to a modern force as the inexpensive and low-tech
explosive-formed penetrators that punched through armored trucks in Iraq.
High-power scramblers that disrupt global positioning systems can make UAV
guidance ineffective and reduce accuracy of smart-weapons. Man-portable air
defense systems are proliferated throughout the world and night-vision optics
of increasing capability are reaching the consumer markets. The A2/AD issue is
not limited to top-tier nations, and unconventional tactics will have to be considered
as well.
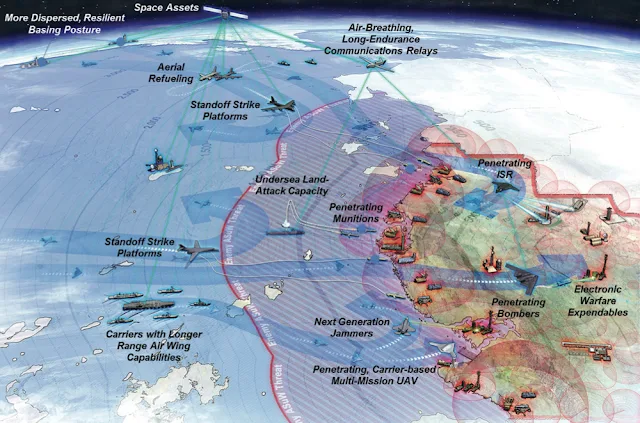
A2/AD creates
a new set of intelligence priorities different than what has been faced in the
last decade. Future A2/AD priorities require some new considerations. According
to a CSBA analyst, a “blinding campaign” or “scouting battle” will be the first
and most important military move in an A2/AD confrontation (Haffa and Datla
2014). A significant change is that ISR assets, or “platforms” as they are
often called, must adapt their sensing capability toward detecting A2/AD forces
and networks in order to survive in these environments (Haffa and Datla 2014).
Additionally, the requirement for high definition FMV with its attendant
bandwidth, which has been so important over the last decade, may take a
backseat to large, strategic UAVs with long-range radar, SIGINT, and EO/IR
sensors and multifunction radio-frequency sensor payloads (Haffa and Datla
2014). Near the beginning of the Iraq and Afghanistan wars, the U.S. was
fielding as few as four UAV “orbits” in theater; in the years that followed, this
peaked to over 60 UAV orbits. The high demand of these types of assets also
created a high demand of bandwidth to transmit and process the data gathered.
The centralized authority, including structures and technologies, employed in
this type of intelligence gathering for the U.S. “processes more than 1.3
petabytes of data a month—equivalent to 1,000 hours a day of full-motion 11
video—and better sensor technology will only add to these figures” (Schanz
2013, 24). Data management and movement are vital to operations where control
of air, sea, and space is contested, according to USAF leaders (Schanz 2013).
In addition to
traditional ISR aircraft, America’s most modern fighter aircraft, the F-22 and
F-35, will also have to assume ISR roles well beyond the non-traditional role
(Haffa and Datla 2014). Older fighter and attack aircraft operators learned the
value of using targeting pods for ISR, a process called non-traditional ISR
(NTISR). In the development of the newest generation of aircraft, ISR
capabilities were included in the capabilities of these multi-role aircraft,
with ISR collection being a dedicated role rather than an ancillary or
additional one. To continue to be able to out-think our adversaries, operators
will have to push these new capabilities well beyond the old NTISR TTPs into
new realms to defeat and circumvent A2/AD systems. Airborne platforms are not
the only way to move ISR assets over enemy territory quickly and safely.
Space-based systems have been in use by the United States for over half a
century. The Corona program began in 1959 and since then the U.S. has deployed
vast constellations of reconnaissance satellites into orbit. While satellite
reconnaissance was considered critical during the Cold War, it has not been
considered a major player in recent years in the pursuit of high-value, mobile,
tactical targets.
However, space-based radar and IR collection will prove to be
particularly significant for defeating A2/AD (Haffa and Datla 2014). Similar to
the airborne fleet of ISR, satellite sensors and platforms require robust
space-based communication networks and bandwidth in order to provide essential
ISR integration (Haffa and Datla 2014). All these different assets are operated
under different command structures within the IC: military service commands,
civilian agencies like the Central Intelligence Agency, National Security
Agency, National Reconnaissance Office, and National Geospatial-Intelligence
Agency, and other contracted, partnered, or multinational forces. Whether using
UAVs, manned aircraft, or orbital satellites, in working against A2/AD, the
United States must pay greater attention not only to joint interoperability
in the processing, exploitation, and dissemination (PED) process but also to
their security (Haffa and Datla 2014).
With all these
new priorities, it is reasonable to ask how the current U.S. systems measure up
to new requirements. In an A2/AD environment, quickly projecting military power
may hinge on the fighting forces’ ability to eliminate A2 and AD systems in the
span of a few hours or days. There are considerable risks in doing so,
particularly in the absence of long-range, penetrating surveillance
(Krepinevich, Watts and Work 2003). High-altitude, long-endurance UAVs will
play a role, but depending on the enemy’s airstrike and air-defense capability,
will have to be operated carefully and be equipped with self-defense
capabilities (Haffa and Datla 2014). The purpose-built ISR capabilities of the
F-22 and F-35, combined with their low observability, could make them primary
ISR collectors in contested airspace (Haffa and Datla 2014).
Despite the
changing environment, Lt. Gen. James said that the USAF’s force structure for
ISR will not see significant change in the near term, and many of the assets
used in U.S. Central Command (Middle East region) will also see a great deal of
use in the Asia-Pacific region (Schanz 2013). This ignores or glosses over the
fact that the joint force has yet to come to grips with the challenges and
range of possible options to employ ISR platforms in contested airspace (Haffa
and Datla 2014)
References:
- Krepinevich, Andrew, Barry Watts, and Robert Work. Meeting the Anti-Access and Area-Denial Challenge. Washington, D.C.: Center for Strategic and Budgetary Assessments, 2003.
- Olson, Wyatt. "Mideast Flare-up, Budget Cuts Could Affect Pacific Pivot." Stars and Stripes. September 22, 2014. http://www.stripes.com/news/pacific/mideast-flare-up-budget-cuts-could-affect-pacificpivot-1.304295 (accessed October 15, 2014).
- Schanz, Marc V. "ISR after Afghanistan." Air Force Magazine: The Online Journal of the Air Force Association, January 2013: 22-27.
- United States Department of Defense. "Air-Sea Battle: Service Collaboration to Address Anti-Access & Area-Denial Challenge." 2013.
Publication Details:
This work is
an extract from an article titled "Intelligence Operations in Denied Area by
Jeff Cuddington", VOL 2, NO 1, (2015): AT
HOME AND ABROAD: Thinking Through Conflicts and Conundrums, licensed under a Creative
Commons Attribution 3.0 License. ISSN: 2377-1852
Download the Paper - LINK